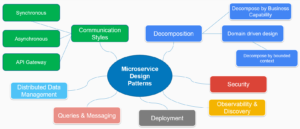
Microservices architecture has revolutionized the way we design and build software systems, providing scalability, flexibility, and agility. However, the distributed nature of microservices introduces unique security challenges that require careful consideration. In this article, we’ll explore essential microservices security best practices to safeguard your distributed systems effectively.
1. Authentication and Authorization
1.1 Token-Based Authentication
Implement token-based authentication for microservices communication. OAuth 2.0 and JSON Web Tokens (JWT) are popular choices. This ensures that only authenticated and authorized requests are processed, mitigating unauthorized access.
1.2 Role-Based Access Control (RBAC)
Enforce RBAC to manage permissions effectively. Assign roles to users or services and grant permissions based on these roles. This principle applies not only to user-facing applications but also to internal microservices interactions.
2. Transport Layer Security (TLS)
Use TLS for secure communication between microservices. Encrypting data in transit prevents eavesdropping and man-in-the-middle attacks. Ensure that all communication channels, both internal and external, are secured with TLS.
3. API Gateway Security
3.1 Rate Limiting
Implement rate limiting at the API gateway to protect against abuse, denial-of-service attacks, and to ensure fair usage of resources. This helps maintain the stability and availability of your microservices.
3.2 Authentication at the Gateway
Authenticate requests at the API gateway before they reach the microservices. This centralizes authentication logic and adds an additional layer of security, protecting microservices from unauthorized access.
4. Service-to-Service Communication Security
4.1 Mutual TLS
Employ Mutual TLS (mTLS) for service-to-service communication. This ensures that both the client and server authenticate each other, adding an extra layer of security to prevent unauthorized services from communicating.
4.2 Secure Service Discovery
Use secure service discovery mechanisms to ensure that only authorized services can discover and communicate with each other. This prevents rogue services from compromising the integrity of the entire system.
5. Data Protection
5.1 Encryption at Rest
Encrypt sensitive data at rest to protect it from unauthorized access. Implement encryption mechanisms for databases and storage systems, ensuring that even if the physical storage is compromised, the data remains secure.
5.2 Input Validation
Implement robust input validation to prevent injection attacks. Validate and sanitize inputs at the microservices entry points to mitigate common vulnerabilities such as SQL injection and cross-site scripting (XSS).
6. Logging and Monitoring
6.1 Centralized Logging
Implement centralized logging to monitor and analyze security-related events across microservices. This aids in identifying suspicious activities, detecting anomalies, and responding to security incidents promptly.
6.2 Real-time Monitoring
Utilize real-time monitoring to detect unusual patterns or behaviors in your microservices architecture. Anomaly detection can help identify security threats before they escalate.
7. Container Security
7.1 Image Scanning
Scan container images for vulnerabilities before deployment. Implement container security best practices, such as regularly updating base images and ensuring that only trusted images are used in your microservices environment.
7.2 Runtime Security
Employ runtime security measures for containers. This includes restricting container privileges, monitoring container activities, and using tools that detect and respond to suspicious behavior within containers.
8. Continuous Security Testing
Integrate security testing into your continuous integration and continuous deployment (CI/CD) pipelines. Perform regular security assessments, including static code analysis, dynamic application security testing (DAST), and penetration testing, to identify and remediate vulnerabilities.
Conclusion
Securing microservices requires a holistic approach that addresses the unique challenges posed by distributed systems. By following these microservices security best practices, you can establish a robust security posture that protects your applications, data, and users. As the threat landscape evolves, staying informed about emerging security trends and continuously updating your security measures is crucial for maintaining a resilient and secure microservices architecture.