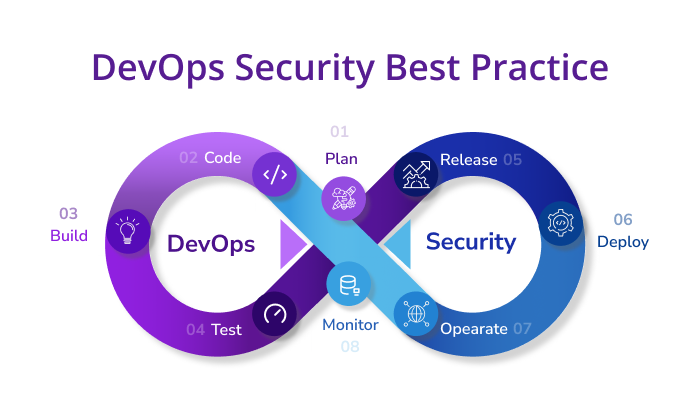
DevOps has revolutionized software development and deployment by fostering collaboration, automation, and efficiency throughout the development lifecycle. However, as organizations embrace DevOps practices, security becomes a paramount concern. Securing the DevOps pipeline is crucial to ensure that applications are developed, tested, and deployed with the highest level of security. In this article, we’ll explore best practices for securing your DevOps pipeline to protect your applications and data.
1. Code Repository Security:
a. Access Control:
Ensure proper access controls on your code repositories. Only authorized personnel should have write access, and read access should be granted on a need-to-know basis.
b. Code Signing:
Implement code signing to verify the integrity and authenticity of your source code. This ensures that only trusted code is introduced into the pipeline.
2. Build Server Security:
a. Build Isolation:
Run builds in isolated environments to prevent contamination from previous builds. Containers or virtual machines are often used to achieve this isolation.
b. Dependency Scanning:
Regularly scan dependencies for known vulnerabilities. Use tools like OWASP Dependency-Check to identify and remediate security issues in your third-party libraries.
3. Continuous Integration (CI) Security:
a. Automated Testing:
Implement automated security testing as part of your CI process. This includes static application security testing (SAST) and dynamic application security testing (DAST) to catch vulnerabilities early.
b. Security Gates:
Introduce security gates in your CI/CD pipeline. A security gate ensures that code meeting specific security criteria is allowed to proceed to the next stage.
4. Artifact Repository Security:
a. Access Controls:
Apply strict access controls to your artifact repositories. Limit write access and tightly control permissions to prevent unauthorized changes.
b. Artifact Signing:
Sign your artifacts to ensure that only trusted and unaltered artifacts are deployed. This prevents tampering with the artifacts during the deployment process.
5. Deployment Security:
a. Immutable Infrastructure:
Embrace the concept of immutable infrastructure where deployments are treated as disposable. This reduces the attack surface and makes it easier to roll back in case of security issues.
b. Configuration Management:
Secure your configuration management by using tools that support encryption and secure storage of sensitive information. Avoid hardcoding secrets in configuration files.
6. Continuous Monitoring:
a. Logging and Auditing:
Implement thorough logging and auditing throughout your pipeline. This helps in identifying and investigating security incidents.
b. Security Analytics:
Utilize security analytics tools to analyze logs and detect anomalous patterns. This can help in identifying potential security threats or breaches.
7. Infrastructure as Code (IaC) Security:
a. Template Security:
Secure your infrastructure templates by following best practices for the Infrastructure as Code. Regularly review and scan your templates for security vulnerabilities.
b. Parameterization:
Parameterize sensitive information in your infrastructure code, such as credentials and API keys. Store these parameters securely and avoid hardcoding them.
8. Access Management:
a. Least Privilege Principle:
Follow the principle of least privilege for all accounts and services involved in the DevOps pipeline. Only grant the minimum level of access necessary for each entity to perform its function.
b. Secrets Management:
Implement a robust secrets management solution to securely store and distribute sensitive information such as API keys, passwords, and certificates.
Conclusion
Securing your DevOps pipeline is an ongoing process that requires a combination of best practices, tools, and a security-first mindset. By incorporating security measures at each stage of the development lifecycle, from code repositories to deployment, you can significantly reduce the risk of security vulnerabilities and breaches. Regularly review and update your security practices to stay ahead of evolving threats and ensure that your DevOps pipeline remains a stronghold for secure and efficient software development and delivery.